- An identity provider (IdP), such as Microsoft Entra ID (Entra ID). The same approach applies to other identity providers that support token exchange and Single Sign-On (SSO).
- A third-party enterprise application, like Workday.
- An application that hosts the embedded chat
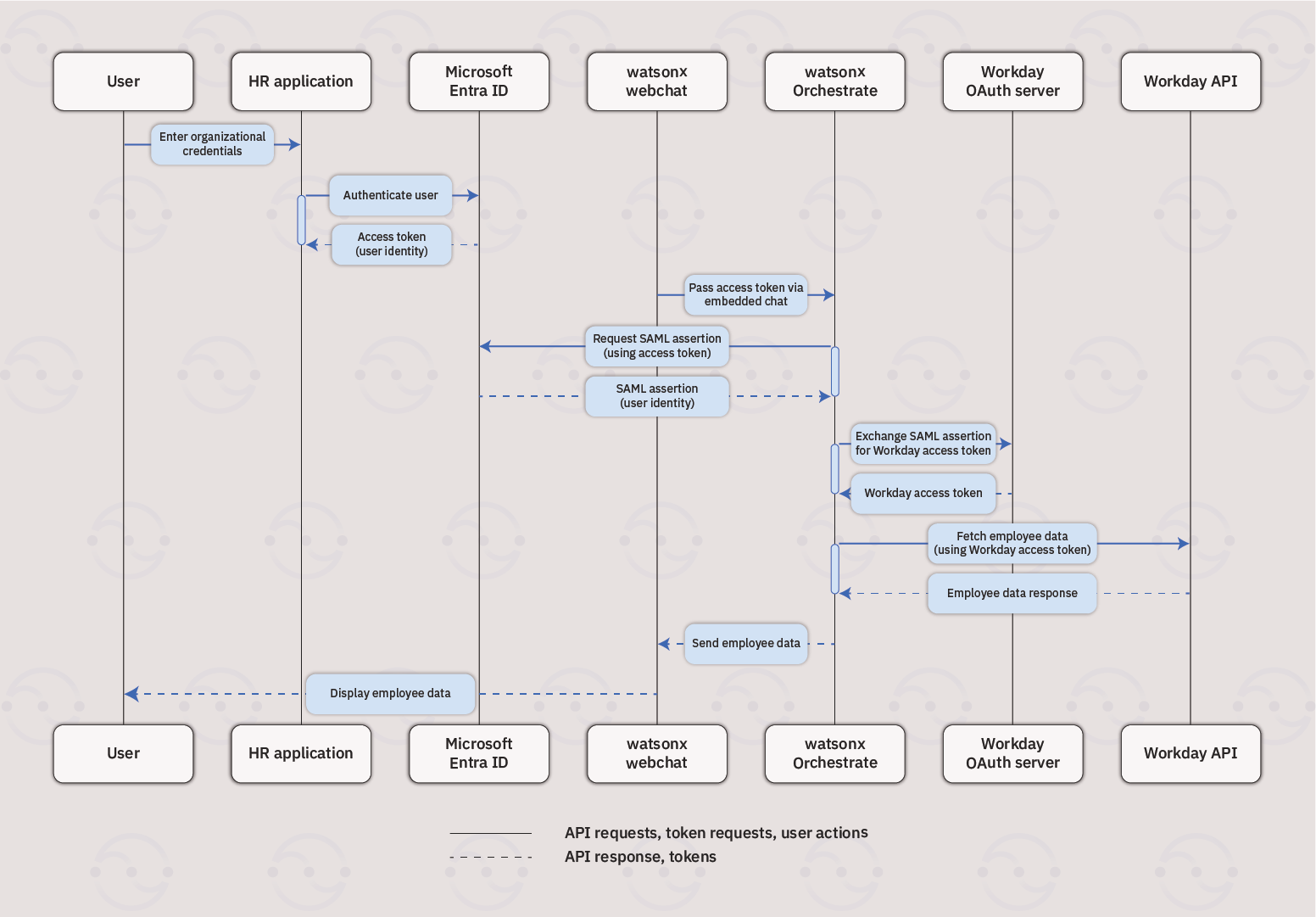
Flow summary
- User authentication: The user logs in to the application that hosts the embedded chat by using their own credentials. The IdP authenticates the user and returns an access token.
- Token propagation through embedded chat: The application that embeds watsonx Orchestrate web chat and receives the access token from IdP and passes it to watsonx Orchestrate.
-
Exchange tokens:
IBM watsonx Orchestrate:
- Requests a SAML assertion from the IdP by using the access token.
- Exchanges the SAML assertion for an access token from the enterprise application’s OAuth server.
- API access: IBM watsonx Orchestrate uses the enterprise app’s access token to call its API, for example, Workday API, and retrieves data.
- Response: The API response is returned to the user through the embedded chat in the application.
Tutorial: Connecting watsonx Orchestrate to Workday using Entra ID
The tutorial guides you to configure Single Sign-On (SSO) for Workday using Entra ID and the OAuth 2.0 On-Behalf-Of (OBO) flow with watsonx Orchestrate. This integration allows you to manage authentication centrally while giving users direct, secure access to Workday without separate logins.Before you begin
Make sure that you have:- The application or web page where the embedded chat is hosted and registered with Entra ID and configured with the appropriate API permissions.
- Client credentials for Workday API, such as client ID and secret.
- Admin or Builder access to your watsonx Orchestrate instance.
- The watsonx Orchestrate Agent Development Kit (ADK) installed and authenticated.
- To install ADK, see Installing the watsonx Orchestrate ADK and Installing the watsonx Orchestrate Developer Edition.
Steps for configuring SSO authentication between watsonx Orchestrate and Workday
Make sure that the SSO authentication is configured between Entra ID and Workday. Use the watsonx Orchestrate ADK (Agent Development Kit) to set up the OAuth 2.0 OBO flow. This configuration allows token exchange between Entra ID and Workday. a. Set up the connection between Workday and watsonx Orchestrate.- You can either use a configuration file or CLI commands to set up the connection.

